There are following things to remember
1. There are three parties involved in this process overall
a. Client : You, who want to access FileServer (Principal)
b. KDC (It is made of two components)
i. Authentication Service
ii. Ticket Granting Service
c. FileServer : The actual resource which you want to access
2. In total 3 Secrete keys (1 for Client, 1 for File Server, 1 for KDC itself): Which never ever travels over the network.
a. Client key resides on client machine as well as KDC
b. Server Key resides on the Server machine as well as KDC
c. KDC key resides only on KDC machine
Client Machine
|
File Server Machine
|
KDC Machine
|
|
Client Key
|
Yes
|
Yes
|
|
Server Key
|
Yes
|
Yes
|
|
KDC Key
|
Yes
|
3. Total
2 Session keys, will be generated during the process and valid only for
8 hours session. (They will travel over the network and data is
encrypted by these keys when communication happens between client and
KDC ,client and File Server).
a. Client and KDC communication (Encrypted by Session Key 1)
b. Client and FileServer communication (Encrypted by Session key2)
How overall process works
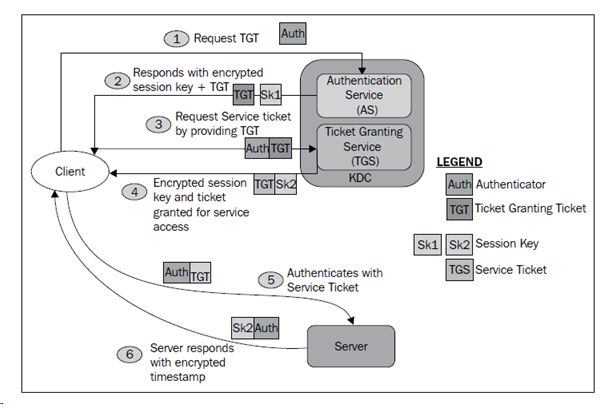
1. Client/You want to access the FileServer in the network, but you are not authenticated user at first.2. You will send a request for getting “Ticket Granting Ticket” from the KDC.
a. While sending the request your message will be encrypted by the Client Secrete key which, is only available with you and KDC.
b. KDC checks its database whether you are real user or not and find the secrete key to decrypt your message.
3. Now KDC will create TGT (Ticket Granting Ticket for you, this TGT is encrypted by KDC key and owned by KDC only) and a Session Key (S1).
a. Bundle Both TGT+S1 and encrypt the bundle with user key and send to the client.
4. Now at client side, this bundle will be decrypted using Client Key. However, TGT cannot be decrypted because it is encrypted by KDC Key.
5. Client will have to request the Service Ticket, so it can access the FileServer
a. Client create a Authenticator object and encrypt it with Session Key1
b. Bundle the TGT+Authnticator+request for FileServer and send to the KDC
6. Now at KDC side, as it checks the bundle and find out that
a. TGT was not touched/altered in between great
b. Using session key (S1) decrypt the Authnticator and verify the client, great
c. And see that user need access to FileServer
7. KDC will create a Service Ticket (Encrypted by Server Key, which is owned by only FileServer and KDC) and another session key S2. The bundle now contains the (Service Ticket + Session Key 2)
a. This bundle is encrypted by S1 (First Session key ) and sent to the client,
8. At client side bundle will be decrypted using first Session key S1
a. Service Ticket (Can not be decrypted by client as it is owned by FileServer and client does not have it)
b. Session Key (S2, second one, will be used for communication between client and server)
9. Now Client has the ticket to request file server.
a. Client Prepare a bundle (Server Ticket+Authenticator+Session Key s2)
b. Send this bundle to File server
10. At server side bundle will be opened
a. Server will check service ticket is encrypted by Server key and not impacted/touched.
b. It will authenticate the user and send the acknowledgement to client.
11. Now client and servers are authenticated and whatever communication happens between client and server will always by encrypted using session key (S2)